 Internet Voting For Military Is An Open Invitation To Election Fraud
Internet Voting For Military Is An Open Invitation To Election Fraud Internet Voting For Military Is An Open Invitation To Election Fraud
Internet Voting For Military Is An Open Invitation To Election Fraud| EJF Home | Where To Find Help | Join the EJF | Comments? | Get EJF newsletter |
| Vote Fraud and Election Issues Book | Table of Contents | Site Map | Index |
| Chapter 3 — Direct Recording Electronic Voting |
| Next — Internet Voting Revisited by David Jefferson, Avi Rubin, Barbara Simons, and David Wagner |
| Back — All The President's Votes? by Andrew Gumbel |
DoD votes for Accenture's eDemocracy
Saudi/Yemen link to online election company
Offshore company captures online military vote
U.S. to test expat cybervoting
A security analysis of the Secure Electronic Registration and Voting Experiment (SERVE)
In early 2003 it was found that the U.S. Department of Defense (DoD) had embarked on a large-scale program to provide Internet voting for military and government officials stationed outside the continental United States. That immediately raised every red flag anyone familiar with computer voting could wave.
Having helped defeat Internet voting in Colorado in February 2001 (see letter by Dr. Corry to Senator Nichol) the intent of the Secure Electronic Registration and Voting Experiment (SERVE) program was felt by the Equal Justice Foundation to have grave implications for the future of voting. There is no known method by which Internet voting can be made secure, provide a secret ballot, ensure that only the eligible citizen voter is submitting the ballot, or prevent fraudulent votes from being transmitted. Such systems are also subject to denial of service attacks that could well disrupt the entire voting process.
There were also grave concerns with the contractors working on the SERVE program, as recorded below. Many of the investors in the contracting companies, who often appeared to have controlling interest, were foreign nationals, and Accenture is based offshore. It was clear the program had all the ingredients for a disaster.
Internet voting was also proving to be very expensive with initial costs running around $70,000+ per ballot cast. The second year of the program promised to lower costs to just several thousand dollars per ballot.
Normally, DoD programs are virtually unstoppable, and seven states had signed up to participate in the second year of trials. But a series of damning revelations about computer voting apparently convinced Pentagon officials to seek an independent review of the program. Remarkably, after expending only $22 million, the security experts cited below convinced the DoD to cancel the program just one day before voting trials were to begin.
Below the life and death of SERVE is outlined. However, the DoD is now (June 2006) resurrecting the idea of Internet voting in the form of email balloting, an even stupider and less secure method. But about six states, including Colorado, have passed legislation permitting email voting.
© 2003 Internetnews.com
Reproduced under the Fair Use exception of 17 USC § 107 for noncommercial, nonprofit, and educational use.
July 7, 2003 — Just a month after acquiring election.com, IT consulting firm Accenture has won a contract with the Department of Defense (DoD) to establish trial Internet voting for overseas U.S. personnel for the 2004 elections. Terms of the contract were not disclosed.
Accenture will support the DoD's Federal Voting Assistance Program (FVAP) in the a Secure Electronic Registration and Voting Experiment (SERVE), which Congress has mandated as way to improve voting opportunities for Americans.
The SERVE program allows for absentee balloting for U.S. personnel using any Windows-based computer with an Internet connection.
To serve DoD clients and others in the government, Accenture launched a new business called eDemocracy Services that is focused on delivering services to election agencies around the world. eDemocracy Services will provide strategy and planning, program management, election systems management, voter registration systems development, and transformational outsourcing services and solutions.
"We created our elections practice in response to the market need that emerged following the 2000 elections, and we continue to see tremendous global business opportunities in the election industry," said Steven J. Rohleder, group chief executive of Accenture's Government operating group."
Rohleder added, "Formalizing this practice as a business is consistent with our strategy to expand our services into key areas of government where we have the experience and capabilities to deliver high-value solutions that meet the needs of our clients."
Previously a strategic alliance partner with Accenture, election.com has implemented its election systems management software in more than 170 U.S. counties and several U.S. states. Election.com also helped deliver the first legally binding public Internet elections in France specifically for French expatriates.
In the U.S., Accenture developed Florida's Central Voter Database (CVD), which was used during the 2002 mid-term elections. The CVD serves as a repository of all State of Florida voter registration information and provides local county election officials with the information to determine a voter's eligibility.
In the United Kingdom, Accenture plans on building on election.com's participation in election modernization pilots in May 2002 and 2003.
The pilots were part of the Office of the Deputy Prime Minister's commitment to make it easier and more convenient for citizens to engage with government. Key elements of the program included Internet, phone and public access kiosk voting; smart card deployment for voter authentication; and real-time, online voter registration rolls. [EJF note: All these projects proved to be disasters.]
© 2003 Newsmax.com
Reproduced under the Fair Use exception of 17 USC § 107 for noncommercial, nonprofit, and educational use.
Friday, May 30, 2003 — Election.com, a privately held New York-based election software firm, currently holds a contract with the Defense Department to provide online absentee ballot voting for the U.S. military in 2004.
However, Election.com also recently revealed that its majority stockholders were a group of Saudi businessmen who did not want their names to be known.
According to a February 2003 article published in Newsday by Mark Harrington, in "a letter sent to a select group of well-heeled Election.com investors January 21, the online voting and voter registration company disclosed that the investment group Osan Ltd. [no known web site] paid $1.2 million to acquire 20 million preferred shares to control 51.6 percent of the voting power."
According to the Newsday article, Osan Ltd. purchased "passive control" of Election.com using money obtained from foreign sources. Osan Ltd. is described as an investment group made up of unnamed Saudi businessmen.
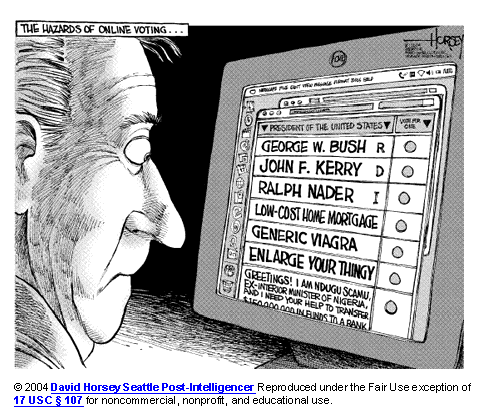
However, Osan may not be a Saudi firm after all. According to information provided by the Yemen Ministry of Trade, Osan Investment is reportedly located in the city of Sanaa, inside Yemen.
Yemen is the family home of Osama bin Laden and is currently regarded by intelligence officials as a haven for members of the al-Qaeda terrorist group. The State Department continues to warn U.S. citizens to defer travel to Yemen.
According to the State Department,
"the September 11 terrorist attacks in the United States elevated security concerns for Americans in Yemen that already were high, following a number of terrorist actions and kidnapping incidents over the past few years."
"Previous incidents included the October 2000 attack on a U.S. Navy vessel in port at Aden, which resulted in the death of 17 American servicemen and women, and the December 1998 kidnapping of 16 Western tourists, four of whom were killed in a clash between the terrorists and Yemeni government forces. Further, armed tribesmen in Yemen have kidnapped a number of foreigners in attempts to resolve disputes with the Yemeni government."
The Election.com link to anonymous Saudi money raised the possibility that a U.S. government contract might be funding terrorist operations. The questionable ownership status is now about to change the Garden City election company.
According to a source inside Election.com, a major shake-up in company ownership is about to take place that "will render the Saudi story a moot point." The source, who requested anonymity, stated that the Election.com ownership would change by early next week.
Election.com currently has a contract with the Federal Voter Assistance Program and is slated to provide online absentee ballot voting for the U.S. armed services. The online voting is expected to be ballotless and completely electronic.
The online voting company also teamed with Accenture Corporation to win a five-year, multimillion-dollar contract from the Commonwealth of Pennsylvania's Department of State to build and deploy a centralized voter registration and election management system using Election.com's Election Systems Manager software.
The system, designed to help election officials in Pennsylvania's 67 counties maintain accurate and reliable voter registration records, will be known as the Statewide Uniform Registry of Electors system, or SURE.
Accenture officials confirmed that they were aware of the ownership situation with Election.com.
"We talked to Election.com about their structure," stated Accenture spokesman Peter Soh.
"We are aware of Election.com's ownership status — as is our client, the Commonwealth of Pennsylvania. Osan Ltd. is an investment firm made up of Saudi and other foreign investors. They are passive investors only. Election.com is run by U.S. employees," stated Soh.
Despite the reassurances, the sudden change in Election.com's ownership comes only after questions were raised surrounding Osan Ltd. and whether it is a Saudi or Yemeni company.
There are also many questions about Election.com's capability to provide accurate and reliable election services. Election.com recently provided online Internet voting for Canada's National Democratic Party (NDP).
However, the NDP voting in January 2003 was disrupted by a computer hack attack as thousands across the country tried to log on and cast ballots using the Internet.
According to a report published by the CBC, Earl Hurd of Election.com said he believed that someone used a "denial of service" program to disrupt the voting, "paralyzing the central computer by bombarding it with a stream of data."
The accuracy of Election.com's Internet voting software has also come under fire. One Canadian voter rights advocate has challenged the "ballot less" software provided by Election.com.
"Party leadership races are not controlled by provincial statute. All parties have used alleged, unverifiable, bogus, ballot less, telephone — Internet voting for their leadership — primary races," stated Brent M.P. Beleskey the director of the Canadian International Voters Coalition.
"Speaking as a Canadian, the invasion of the Election.com alleged ballot less computerized Internet voting is a corporate crime against my sacred freedoms and liberties. Since November 2000 when a CBC documentary was aired across Canada, of which Election.com was interviewed, I have put forth a challenge on the creditability of Election.com and other election corporations like them. And have heard no response to my allegations," stated Beleskey.
© 2003 Lynn Landes
Reproduced under the Fair Use exception of 17 USC § 107 for noncommercial, nonprofit, and educational use.
July 16, 2003 — Last year, while President Bush marshaled U.S. forces for the invasion of Iraq, the patriots at the Department of Defense awarded the contract for a new online voting system for the military...to an offshore company.
Secure Electronic Registration and Voting Experiment (SERVE) is the system and Accenture (formerly Andersen Consulting of Enron bankruptcy fame) is the company. And although Accenture has not been officially implicated in the Enron scandal, they have created a reputation of their own that is already raising eyebrows.
The Canada-based Polaris Institute published a scathing report on Accenture, saying, "Accenture's efforts in government outsourcing have often been very expensive and/or of poor quality.There is good reason to question Accenture's track record in outsourcing of government services."
Accenture is the leading offshore beneficiary of government contracts whose main business is the privatization of government services, according to Lee Drutman of Citizen Works, a non-profit founded by Ralph Nader. Accenture has a troubling track record, a close business relationship with Dick Cheney's Halliburton, and 2500 partners — more than half are not U.S. citizens.
Since 2001 Accenture and Election.com have been strategic partners "... to jointly deliver comprehensive election solutions to governments worldwide," according to their press release. Last month Accenture bought the public-sector election assets of Election.com, which suffered its own scandal this year when it was discovered that Osan Ltd., a firm of Saudi and other foreign investors, bought controlling interest in it.According to Mark Harrington of NewsDay.com, "Several shareholders of the company said they were surprised by the recent buyout and have asked for securities regulators to investigate."
Election.com has had other problems. In January 2003, during Canada's New Democratic Party leadership convention, the Canadian Broadcasting System reported, "Earl Hurd of Election.com said he believes someone used a 'denial of service' program to disrupt the voting - paralyzing the central computer by bombarding it with a stream of data" . — service was restored, then — "Toronto city councilor Jack Layton's victory on the first ballot surprised many, who had expected a second or even third round of voting before a leader was chosen from the pack of six candidates."
For election security experts, a strong and growing suspicion is that computer glitches or disruptions are actually vote rigging. A surprise election result should raise a red flag.
Accenture is big. It has more than 75,000 employees in 47 countries, and generated net revenues of $11.6 billion for the fiscal year ended Aug. 31, 2002. On their Board of Directors is Steve Ballmer, Microsoft's CEO and known to many as Bad Boy Ballmer for his ruthless, if not illegal, business practices.Microsoft has been sued by the federal government and several states for monopolistic business practices which were designed to destroy their competition. Massachusetts's Attorney General is still pursuing Microsoft.In March 13, 2000Andersen Consulting (now Accenture) and Microsoft signed a "$1 Billion Pact To Form Joint Venture and Expand Global Alliance." What's the alliance? To control voting systems around the world?
A sense of civic duty isn't high on Accenture's list of priorities. According to an article last year in TheDailyEnron.com, "Accenture is lobbying furiously on Capitol Hill to defeat a measure that would deny federal contracts to US companies that move offshore to escape US taxes. Accenture, you see, has incorporated in Bermuda. But, Accenture also holds nearly $1 billion in government contracts in the US. The company earned nearly $700 million last year working for Uncle Sam and — ironically — is currently under contract with the Internal Revenue Service itself to redesign its online and Internet operations."
Then there's the Accenture connection to Halliburton, vice president Dick Cheney's former employer. Halliburton is widely criticized for doing business with brutal regimes and was the subject of a SEC investigation and several lawsuits surrounding their accounting practices during and after Cheney's tenure at the helm.The Polaris Institute says that in July 2000 David Lesar succeeded Dick Cheney as Chairman and CEO of Halliburton Company.Before joining Halliburton, Lesar was employed by the Arthur Andersen, Accenture's former parent company. Polaris says, "...while defending Halliburton's accounting practices, David Lesar publicly acknowledged that Cheney knew about the firm's accounting practices..."
In an October 2001 press release, Halliburton and Accenture announced a major expansion of their longstanding relationship with the signing of an alliance between Accenture and Landmark Graphics Corporation, a wholly owned business unit of Halliburton.
And unlike the words of the U.S. military's anthem, "I'm proud to be an American," Accenture owes its allegiance to "partners" outside of the USA.
In a letter to the editor of the Austin Chronicle last year, Accenture's Director of Corporate Communications, Roxanne Taylor wrote,
"When Accenture's parent company, Accenture Ltd., was first incorporated last year, the organization's 2,500 partners, more than half of whom are non-U.S. citizens, decided to incorporate in Bermuda. With thousands of partners and employees of many nationalities, it was important commercially and culturally for the organization to select a neutral location such as Bermuda for its parent company."
Potentially,6 million U.S. military and civilian voters could soon be using the military's new online voting system.According to computer voting security experts, any online system will be easy to rig by company insiders and vulnerable to attack by outsiders. Apart from that reality, does the U.S. military really want a company owned by non-U.S. citizens in charge of their vote?
Can anyone at the Pentagon spell "national security"?
Lynn Landes is a freelance journalist at EcoTalk.org. Formerly Lynn was a radio show host, a regular commentator for a BBC radio program, and environmental news reporter for DUTV in Philadelphia, Pennsylvania, telephone (215) 629-3553, or email: lynnlandes@earthlink.net
© 2003 International Herald Tribune
Reproduced under the Fair Use exception of 17 USC § 107 for noncommercial, nonprofit, and educational use.
Friday, July 25, 2003, Washington, D.C. — As many as 100,000 American military personnel and civilians abroad will have the opportunity to cast their vote via the Internet in elections next year under a new U.S. government plan.
The Defense Department's Secure Registration and Voting Experiment [SERVE] will give registered voters an alternative to the traditional absentee ballot in both the presidential primaries and the 2004 general election as long as their home countries and states participate.
The target audience is only a small portion of the estimated 7.4 million U.S. military and civilians overseas, but it is greatly expanded from a trial online effort in the 2000 election in which fewer than 100 people participated.
"We are trying to reach people who have difficulty voting by mail," said Polli Brunelli, director of the Federal Voting Assistance Program, which is running the project, "and give them [ EJF note: or any hacker] a chance to vote from their personal computer, from a library or even a cybercafé."
The $22 million Pentagon-run experiment is being designed not only to increase voter participation, but also to correct some problems encountered in the hotly contested 2000 presidential election and limit the number of absentee ballots that are disqualified or arrive too late to be counted.
Initially, the program will be limited to registered voters who have access to Microsoft Windows-based computers that can connect to the Internet [ EJF note: the most insecure configuration imaginable with current technology], and are from states and counties that agree to participate in the program.
While the Defense Department has invited all states to participate, so far, Arkansas, Florida, Hawaii, Minnesota, North Carolina, Ohio, Pennsylvania, South Carolina, Utah and Washington have indicated interest. In some states, legislation will have to be changed. If that cannot be done in a timely way, not all of the states listed will be able to participate. A final list is expected to be posted on the Web site, www.serveusa.gov, by the end of July, 2003. [EJF note: Web site taken down.]
The United States joins other countries, including Switzerland and Britain, that have tried electronic voting pilots to reverse declining voter turnout. In the past two years, the Swiss authorities also have used online voting to increase the ease of voting and to attract younger, more technologically savvy voters [EJF note: who will quickly learn how to hack the vote ]. British officials experimented with allowing electronic balloting on local tax issues.
While the proponents say online voting presents a practical and speedy alternative to paper ballots, critics say that there is a strong possibility of voting fraud and Internet viruses corrupting or derailing the process.
"If you have a kiosk under lock and key, it would be a secure site," said John Dunbar, of the nonprofit Center for Public Integrity in Washington, "but if you can vote on the fly with your own laptop, there is no security guarantee."
Dunbar, who wrote a report reviewing the 2000 Pentagon pilot experiment, said it was badly flawed and enormously expensive. The $6 million project cost taxpayers nearly $74,000 per vote.
"The idea is good," he said in an interview, "but if you can't guarantee security you worry about an election being rigged. After all, you are talking about something that is sacred — your vote."
Brunelli said security would be assured through the use of a "digital signature," a procedure to authenticate an actual signature that eligible voters could either get in person at an embassy or consulate or online.
She likened it to military "common access card," which bears the user's photograph and is encrypted to prevent fraudulent use. [ EJF note: And how does a photograph enhance Internet security?]
By going through a series of steps to safeguard the application process, a voter could obtain the digital signature to give him or her access to the paperless process. Other safeguards would include a secure password.
Nevertheless, Brunelli admitted that "there is a whole laundry list of security problems" being tackled by the design company, Accenture, [EJF note: Accenture is registered offshore and a majority of stockholders are Saudi. Accenture is also the successor company to Andersen Consulting of Enron fame. See above article.] and an advisory panel of computer scientists, social scientists and security experts who are looking at the potential threats and measures to mitigate them.
Among the measures being built into the system are intrusion detection, firewalls and tests by "white hat," or friendly, hackers, Brunelli said.
That is still not enough for an electronic voting tabulation expert, Rebecca Mercuri, who called the remote voting project "ridiculous because the whole idea of the Internet is that it is not secure."
She is one of several voting experts who have raised concerns about the confidentiality of voting in cyberspace.
"You open up the system to fraud and manipulation because almost any system can be cracked to expose the voter's identity and ballot open to scrutiny," said Mercuri, who will pursue her specialty at Harvard University's John F. Kennedy School of Government this autumn.
She cited a January 2003 Toronto City Council vote where results were delayed more than an hour because a hacker launched a cyberattack and prevented people from voting by bombarding the Web site with a stream of data. While the computer security wall was not penetrated or the ballot results altered, Mercuri said the incident illustrated the fragility of secure and confidential Internet balloting.
Brunelli insisted that online voting can be made as safe as paper ballots. And, barring some insurmountable security problem that her team has yet to discover, she said such voting was likely to become increasingly commonplace. [EJF note: Now what qualifications does Polli Brunelli have to make such claims?]
. Top
January 20, 2004 — This report is a review and critique of computer and communication security issues in the SERVE voting system (Secure Electronic Registration and Voting Experiment), an Internet-based voting system being built for the U.S. Department of Defense's FVAP (Federal Voting Assistance Program). The program's web site is http://www.serveusa.gov/. While the system is called an experiment, it is going to be used to count real votes in the upcoming general elections. The authors are members of SPRG (the Security Peer Review Group), a panel of experts in computerized election security that was assembled by FVAP to help evaluate SERVE. Our task was to identify potential vulnerabilities the system might have to various kinds of cyber-attack, to evaluate the degrees of risk they represent to the integrity of an election, and to make recommendations about how to mitigate or eliminate those risks.
The SERVE system is planned for deployment in the 2004 primary and general elections, and will allow the eligible voters first to register to vote in their home districts, and then to vote, entirely electronically via the Internet, from anywhere in the world. Besides being restricted to overseas voters and military personnel, SERVE is currently limited to people who vote in one of 50 counties in the seven states (Arkansas, Florida, Hawaii, North Carolina, South Carolina, Utah, and Washington) that are participating. The program is expected to handle up to 100,000 votes over the course of the year, including both the primaries and the general election. (By comparison, approximately 100 million votes were cast in the 2000 general election.) The eventual goal of SERVE is to support the entire population of eligible overseas citizens plus military and dependents. This population is estimated to number about 6 million, so the 2004 SERVE deployment must be judged as a prototype for a very large possible future system.
Our conclusions are summarized as follows:
a. DRE (direct recording electronic) voting systems have been widely criticized elsewhere for various deficiencies and security vulnerabilities: that their software is totally closed and proprietary; that the software undergoes insufficient scrutiny during qualification and certification; that they are especially vulnerable to various forms of insider (programmer) attacks; and that DREs have no voter-verified audit trails (paper or otherwise) that could largely circumvent these problems and improve voter confidence. All of these criticisms, which we endorse, apply directly to SERVE as well.
b. But in addition, because SERVE is an Internet- and PC-based system, it has numerous other fundamental security problems that leave it vulnerable to a variety of well-known cyber attacks (insider attacks, denial of service attacks, spoofing, automated vote buying, viral attacks on voter PCs, etc.), any one of which could be catastrophic.
c. Such attacks could occur on a large scale, and could be launched by anyone from a disaffected lone individual to a well-financed enemy agency outside the reach of U.S. law. These attacks could result in large-scale, selective voter disenfranchisement, and/or privacy violation, and/or vote buying and selling, and/or vote switching even to the extent of reversing the outcome of many elections at once, including the presidential election. With care in the design, some of the attacks could succeed and yet go completely undetected. Even if detected and neutralized, such attacks could have a devastating effect on public confidence in elections.
d. It is impossible to estimate the probability of a successful cyber-attack (or multiple successful attacks) on any one election. But we show that the attacks we are most concerned about are quite easy to perpetrate. In some cases there are kits readily available on the Internet that could be modified or used directly for attacking an election. And we must consider the obvious fact that a U.S. general election offers one of the most tempting targets for cyber-attack in the history of the Internet, whether the attacker's motive is overtly political or simply self-aggrandizement.
e. The vulnerabilities we describe cannot be fixed by design changes or bug fixes to SERVE. These vulnerabilities are fundamental in the architecture of the Internet and of the PC hardware and software that is ubiquitous today. They cannot all be eliminated for the foreseeable future without some unforeseen radical breakthrough. It is quite possible that they will not be eliminated without a wholesale redesign and replacement of much of the hardware and software security systems that are part of, or connected to, today's Internet.
f. We have examined numerous variations on SERVE in an attempt to recommend an alternative Internet-based voting system that might deliver somewhat less voter convenience in exchange for fewer or milder security vulnerabilities. However, all such variations suffer from the same kinds of fundamental vulnerabilities that SERVE does; regrettably, we cannot recommend any of them. We do suggest a kiosk architecture as a starting point for designing an alternative voting system with similar aims to SERVE, but which does not rely on the Internet or on unsecured PC software (Appendix C).
g. The SERVE system might appear to work flawlessly in 2004, with no successful attacks detected. It is as unfortunate as it is inevitable that a seemingly successful voting experiment in a U.S. presidential election involving seven states would be viewed by most people as strong evidence that SERVE is a reliable, robust, and secure voting system. Such an outcome would encourage expansion of the program by FVAP in future elections, or the marketing of the same voting system by vendors to jurisdictions all over the United States, and other countries as well. However, the fact that no successful attack is detected does not mean that none occurred. Many attacks, especially if cleverly hidden, would be extremely difficult to detect, even in cases when they change the outcome of a major election. Furthermore, the lack of a successful attack in 2004 does not mean that successful attacks would be less likely to happen in the future; quite the contrary, future attacks would be more likely, both because there is more time to prepare the attack, and because expanded use of SERVE or similar systems would make the prize more valuable. In other words, a "successful" trial of SERVE in 2004 is the top of a slippery slope toward even more vulnerable systems in the future. (The existence of SERVE has already been cited as justification for Internet voting in the Michigan Democratic caucuses.)
h. Like the proponents of SERVE, we believe that there should be better support for voting for our military overseas. Still, we regret that we are forced to conclude that the best course is not to field the SERVE system at all. Because the danger of successful, large-scale attacks is so great, we reluctantly recommend shutting down the development of SERVE immediately and not attempting anything like it in the future until both the Internet and the world's home computer infrastructure have been fundamentally redesigned, or some other unforeseen security breakthroughs appear. We want to make clear that in recommending that SERVE be shut down, we mean no criticism of the FVAP, or of Accenture, or any of its personnel or subcontractors. They have been completely aware all along of the security problems we describe here, and we have been impressed with the engineering sophistication and skill they have devoted to attempts to ameliorate or eliminate them. We do not believe that a differently constituted project could do any better job than the current team. The real barrier to success is not a lack of vision, skill, resources, or dedication; it is the fact that, given the current Internet and PC security technology, and the goal of a secure, all-electronic remote voting system, the FVAP has taken on an essentially impossible task. There really is no good way to build such a voting system without a radical change in overall architecture of the Internet and the PC, or some unforeseen security breakthrough. The SERVE project is thus too far ahead of its time, and should wait until there is a much improved security infrastructure to build upon.
. Top
| EJF Home | Where To Find Help | Join the EJF | Comments? | Get EJF newsletter |
| Vote Fraud and Election Issues Book | Table of Contents | Site Map | Index |
| Chapter 3 — Direct Recording Electronic Voting |
| Next — Internet Voting Revisited by David Jefferson, Avi Rubin, Barbara Simons, and David Wagner |
| Back — All The President's Votes? by Andrew Gumbel |